Ross Ulbricht's proposed ZeeKans
Why Net Neutrality is not what Big Tech and the Surveillance state wants.
The debate surrounding end-to-end encryption has become increasingly contentious in recent years, with proponents and opponents presenting compelling arguments. One of the key opponents of end-to-end encryption is the deep state, a hypothetical secret government within the United States that operates independently of the elected government. The deep state opposes end-to-end encryption for several reasons, one of which is the potential for shielding criminal activities from government intervention.
Notable individuals such as Ross Ulbricht, Aaron Swartz, and Julian Assange have been associated with promoting end-to-end encryption and are facing legal repercussions. The deep state views their actions as facilitating criminal behavior and hindering law enforcement's ability to access crucial electronic evidence in cases involving cyber intrusions, child exploitation, gang violence, drug trafficking, and terrorism.
The deep state's opposition to end-to-end encryption is rooted in its concerns about public safety and security. Law enforcement agencies require access to encrypted data to effectively combat criminal activities and ensure the safety of citizens. Without lawful access to such data, attributing responsibility for malicious cyber activities becomes arduous, impeding necessary law enforcement responses.
Furthermore, the deep state is apprehensive about the potential implications of widespread end-to-end encryption on global security. In repressive nations where democratic values are under siege, end-to-end encryption has been identified as a tool that makes unfettered surveillance more difficult, thereby protecting freedom of expression and challenging authoritarian governments. While this presents a positive outcome, it also poses a challenge for governments seeking to maintain public safety and security in an increasingly complex digital landscape.
Despite the challenges posed by end-to-end encryption, there is recognition of its importance in safeguarding individual privacy and democratic values. The United States upholds the core values of privacy and protection of essential liberties enshrined in the Fourth Amendment. Striking a balance between leveraging strong encryption to ensure a secure and resilient global internet while enabling law enforcement agencies to fulfill their mandate of protecting citizens from harm is imperative.
The Cyber Solarium Committee's stance on end-to-end encryption has sparked controversy due to its apparent bias towards advocating for government access to encrypted data. While the committee emphasizes the importance of strong encryption for data security, it also raises concerns about the potential hindrance of law enforcement and government agencies in accessing electronic evidence for public safety and security.
One of the key arguments put forth by the committee is the challenge that end-to-end encryption poses to lawful access to electronic evidence in various investigations, including cyber intrusions, crimes threatening serious harms, and terrorism. The committee asserts that attributing responsibility for malicious cyber activity becomes difficult and slow without access to relevant encrypted data content. This argument is based on the premise that end-to-end encryption may impede the government's ability to combat criminal activities and protect citizens from harm.
However, it is essential to critically examine this perspective in light of historical evidence of government overreach and abuse of surveillance powers. The revelations made by Edward Snowden, WikiLeaks' Vault 7 disclosures, and other electronic snooping scandals have exposed the extent to which government agencies have engaged in mass surveillance and exploited vulnerabilities in digital communications. These instances raise serious doubts about the trustworthiness of government access to encrypted data and the potential misuse of such access.
Aadhaar
The Failure of Aadhaar and the Rise of Feudal Techno-Rationing Systems Aadhaar, the world's largest biometric database, has been touted as a revolutionary identification system that would prevent fake people from enrolling on government payrolls. However, the Aadhaar system has faced criticism for its potential to infringe on privacy and human rights. Th…
For example, the Snowden revelations exposed the extensive surveillance practices employed by the National Security Agency (NSA), revealing the agency's mass collection of electronic communications data from both US citizens and individuals around the world. The disclosures highlighted the lack of transparency and oversight in the NSA's surveillance programs, raising concerns about privacy violations and constitutional rights infringements.
Similarly, WikiLeaks' release of Vault 7 documents shed light on the CIA's hacking capabilities and tools, including its ability to exploit vulnerabilities in popular electronic devices and software. These revelations underscored the risks associated with government agencies possessing backdoor access to encrypted communications, as such access can be exploited for covert surveillance and intelligence gathering without proper authorization or accountability.
Moreover, the history of electronic snooping scandals, including the Keystore scandal and instances of unauthorized surveillance, further underscores the need for caution in advocating for expanded government access to encrypted data. The Obama administration's surveillance activities during the 2016 presidential campaign, particularly the monitoring of communications involving then-candidate Donald Trump, raised serious questions about the misuse of surveillance powers for political purposes.
Are We all “precogs” now.
Are We all “precogs” now? Place the following into An Integral analysis framework a Sauserian Framework and Hermenuetic Framework? An Integral Analysis Framework: - The text presents a thought-provoking analysis of global power dynamics, emphasizing the need for a cohesive and united resistance front that transcends traditional paradigms and focuses on fre…
Given this negative evidence and historical context, there is a basis for pessimism regarding the prospect of government agencies, including the NSA, GCHQ, and the 77th Brigade in the UK, acting constitutionally when granted access to encrypted data. The track record of these agencies raises concerns about their adherence to legal and ethical boundaries when conducting surveillance and intelligence operations.
In light of these considerations, it is crucial to critically evaluate the Cyber Solarium Committee's position on end-to-end encryption and its implications for privacy, civil liberties, and democratic values. While recognizing the legitimate concerns about public safety and security, it is essential to weigh these against the potential risks of granting government agencies unfettered access to encrypted communications.
The debate over end-to-end encryption is complex and multifaceted, involving a delicate balance between data security, privacy protection, law enforcement needs, and democratic values. As end-to-end encryption becomes more prevalent, it is imperative to consider its role in safeguarding individual liberties and protecting democratic principles from encroachment by authoritarian regimes.
The United Nations' recognition of end-to-end encryption as a vital tool for pushing back against repressive regimes underscores its significance in defending global freedom of expression and combating high-tech illiberalism. The ability of end-to-end encryption to make unfettered surveillance more challenging in repressive nations highlights its potential to protect democratic values and human rights on a global scale.
In navigating this complex landscape, it is essential to uphold core values that unite citizens of free and open societies, including robust protections for privacy, due process, and constitutional rights. Any government access to encrypted data should be tightly circumscribed by legal safeguards and oversight mechanisms to prevent abuse and ensure accountability.
While acknowledging the dual nature of end-to-end encryption as a tool for both protecting individual privacy and posing challenges to law enforcement, it is crucial to approach this debate with a nuanced understanding of its implications for a free, open, and secure internet. Balancing the imperatives of strong encryption with legitimate law enforcement needs requires a thoughtful consideration of the trade-offs involved and a commitment to upholding fundamental rights and liberties.
In conclusion, the debate over end-to-end encryption necessitates a careful examination of its benefits and challenges, as well as a critical assessment of the implications of granting government access to encrypted data. The historical evidence of government overreach and surveillance abuses underscores the need for caution in advocating for expanded access to encrypted communications. As technological advancements continue to shape the encryption landscape, it is essential to uphold democratic values, human rights, and individual freedoms in navigating this complex terrain.
The ongoing debate surrounding end-to-end encryption necessitates a nuanced approach that considers both the benefits and challenges it presents. While the deep state opposes the widespread adoption of end-to-end encryption due to its potential to impede law enforcement efforts, it is crucial to acknowledge the complex trade-offs involved. As technology continues to evolve and shape the encryption landscape, it is essential for the government and private sector to engage in honest dialogue and seek solutions that align with the fundamental principles of a free, open, and secure society.
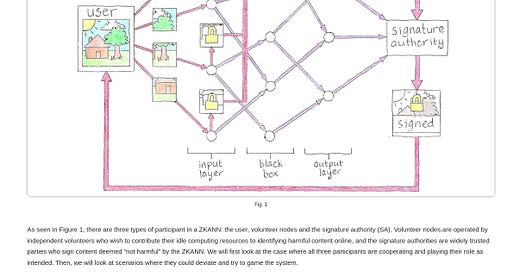
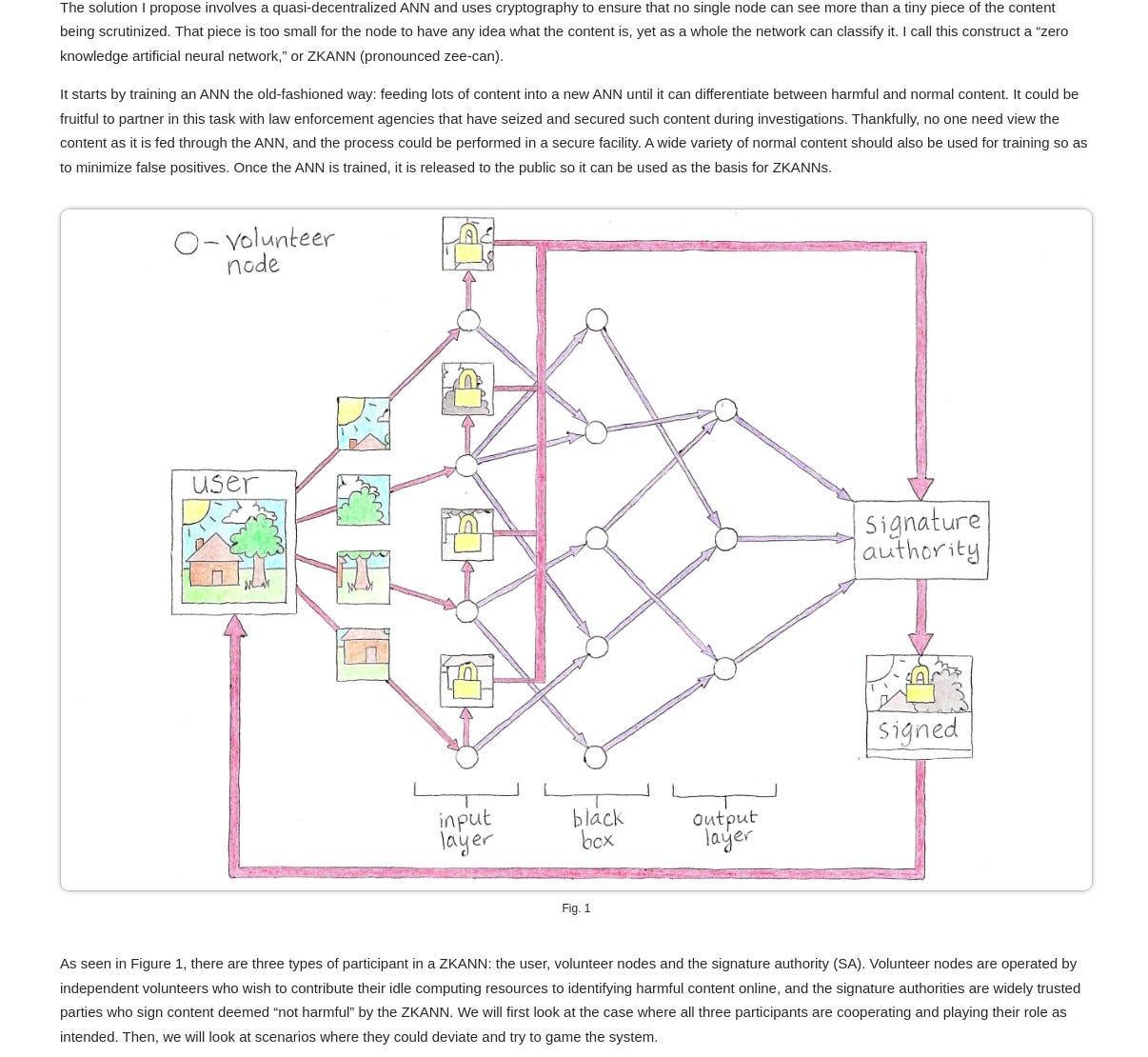
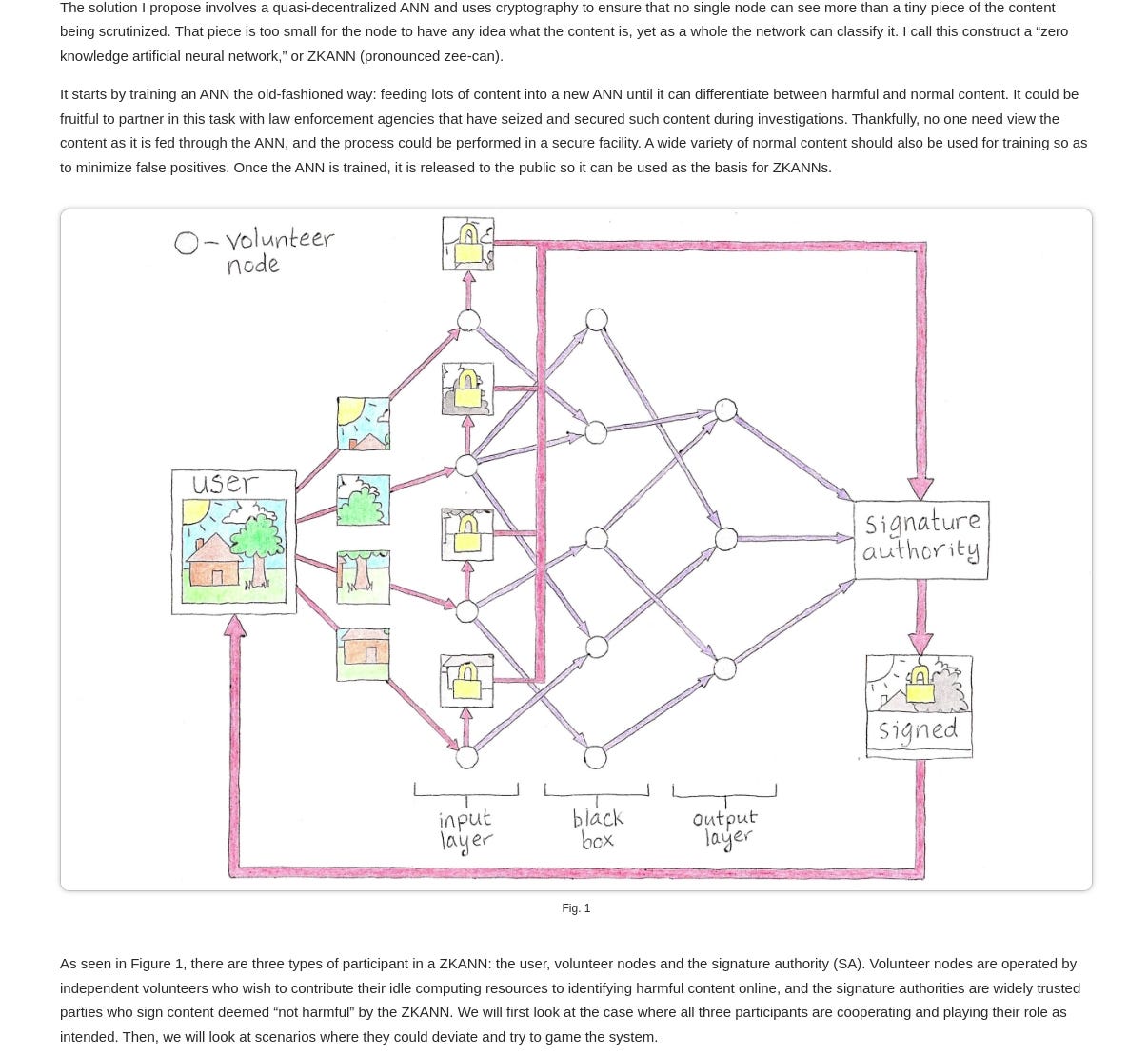
In light of these deep state concerns it is ironic that one of the victims of its paranoia has proposed a workable solution to address those concerns whilst maintaining the privacy of citizens. Ross Ulbrichts proposed solution known as a "zero-knowledge artificial neural network" (ZKANN) has emerged as a potential means to address the content problem associated with end-to-end encryption. ZKANN presents a way to separate harmful content from other encrypted data without compromising individual privacy. This innovative approach combines cryptography and artificial intelligence to create a quasi-decentralized network that can classify content without exposing its details to any single participant.
The ZKANN framework involves three types of participants: users, volunteer nodes, and signature authorities. Volunteer nodes are operated by independent volunteers who contribute their computing resources to identify harmful content online, while signature authorities are trusted parties responsible for signing content deemed "not harmful" by the ZKANN. The process begins with the user selecting a signature authority and a public artificial neural network. Volunteer nodes receive tiny pieces of content from the user, which are then processed through the network without any single participant having access to the complete content.
The ZKANN framework offers a promising avenue for addressing the content problem associated with end-to-end encryption while upholding individual privacy. By leveraging a combination of cryptography and artificial intelligence, ZKANN presents a potential solution that allows for effective content classification without compromising user privacy. However, further development and refinement are required to ensure the independence and integrity of participant nodes within the ZKANN framework.
In conclusion, the debate over end-to-end encryption remains complex and multifaceted, requiring careful consideration of its implications for public safety, individual privacy, and global security. Finding a middle ground that upholds democratic values while addressing law enforcement needs is essential in navigating this complex issue. As technology continues to advance, policymakers must remain vigilant and proactive in shaping a future that balances the benefits and challenges of end-to-end encryption while safeguarding fundamental rights and liberties.
– The intertwining of technology, politics, and governance has created a complex landscape with profound implications for global power dynamics.
– The relationship between tech giants like Google and the US government has raised questions about their influence on global internet access and geopolitical aspirations.
– Pressures faced by organizations like WikiLeaks and the involvement of individuals with ties to the US government underscore the need for continued vigilance in protecting transparency and whistleblowing efforts.
– The emergence of a new kind of empire driven by digital influence and corporate power has reshaped traditional notions of geopolitics and local politics.
– Failures in tech-based governance systems, such as Aadhaar in India and the Post Office Horizon System in the UK, highlight the limitations of centralized command and control systems at large national scales.
SHADOWGATE – WHAT THEY DON’T WANT YOU TO SEE (BY MILLIE WEAVER)
Essentially Ross’s Crime, Aaron Swartz’s crime, and the crime of Julian Assange are making end-to-end encryption a widely available Internet service preventing the extent of monopolisation of the Internet which now exists more than ever.
March 25, 2020
Wrong Kind of Green
“The ruling class exists, it’s not a conspiracy theory. They operate as a class, too. They share the same values, the same sensibility and in Europe and North America they are white. They act in accordance with their interests, which are very largely identical. The failure to understand this is the single greatest problem and defect in left discourse today.”
— John Steppling, Author, Playwright
“This report is crucial reading for anyone interested in creatively considering the multiple, divergent ways in which our world could evolve.”
— Judith Rodin, President of the Rockefeller Foundation
Storytelling. Dystopian scenarios. Not Huxley, Orwell, Bradbury, or Brunner.
#Storytelling.
https://threadreaderapp.com/thread/1242584245887008778.html
Tonight I'm going to share highlights from the 2010 "Scenarios for the Future of Technology & Int'l Development" report produced by The Rockefeller Foundation & Global Business Network. Not just the "Lock Step" scenario, but all 4 scenarios. [54 page report]
Scenario planning for corporate strategy was pioneered by Royal Dutch Shell in the 1970s. [Further reading on scenario planning: The Art of the Long View]The following excerpts are highlights from the May 2010 “Scenarios for the Future of Technology & International Development” report produced by The Rockefeller Foundation & Global Business Network. Not just the more known “Lock Step” scenario, but all four scenarios.
Following “Event 201” (Oct 18, 2019), we must concede that the ruling class has been gifted with phenomenal and prophetic intuitions and insights. (They truly are the chosen ones.)
A WARNING FROM TOMORROW. SOLARIUM FROM IKE TO TRUMP. #COVIDPURPOSE #FOLLOWTHEDEBT #DEBTSERVITUDE #GOODWILLHUNTING #WHERESTHEBEEF #KARLROVE
The cyberspace Solarium report gives ;
THE STATIST TAKE ON END-TO-END ENCRYPTION, IN A NUTSHELL “NOT FOR THE PLEBS”
https://drive.google.com/file/d/1ryMCIL_dZ30QyjFqFkkf10MxIXJGT4yv/view
THE SIX WAYS ON SUNDAY, CARBON CURRENCY END GAME 16 TO 1 ON, WHAT ARE THE ODDS OF THAT?. R &R DISCUS
https://notthegrubstreetjournal.com/2022/02/06/the-six-ways-on-sunday-carbon-currency-end-game-16-to-1-on-what-are-the-odds-of-that/
If one observes the long game the dominant Narrative of the past 30 years is Climate Change and CO2 emission being the only thing anyone needs to focus upon. The Carbon footprint narrative is, by a long chalk, well ahead of the curve even with the relatively short but seemingly endless Pandemic and Vaccine Narratives of the Past two years.
Naming names, Larry Fink of Blackstone and Blackstones Going Direct is considerably more powerful a control lever on what happens next than the efforts of Bill Gates and Dr. Fauci to enrich Big Pharma and themselves, Gates also has a bigger card in the game, and that is Digital ID and its relationship to both Near earth Satellite networks and the 5G networks, which coincidentally really were rolling out at the Same Time as the Wuhan Event, also in coincidentally, Wuhan.
The Vaccines and Vaccine injuries are very closely related to the adjuvant and not necessarily the Pathogen dose delivered in the solution of the Adjuvant. It is the Adjuvant rather than the disease that is of interest to the 5G / ID aspects of what the past two years have been all about.
The Repo Spike in Newyork on September 19th was the starting pistol, of course, the dress rehearsal was Event 201, The Objective was almost certainly to gain widespread acceptance of Digital IDs on SmartPhone devices and possibly by stealth through Nanotechnology, within the Adjuvant solutions in the mRNA vaccines( Experimental Gene Therapies?).
So what about Climate Change, CO2, and all that, no it’s not the Graphine found in some adjuvant samples but the Rationing of Carbon through a Carbon-based currency which is why the Climate Change Agenda particularly the CO2 control knob is so important.
The ratio of Good Energy ( renewables) for which Carbon Credits will be created and Bad Energy of “Fossil Fuels which represent Carbon debits, is 16:1. There are various combinations that could see the ratio vary but essentially as with The Gold Standard a Carbon Credit Renewables Standard has the same ratio as the Historical Bi-Metallic ratio known to numasticist’s the world over. A deflationary centralised banking regime will be able to impose Austerity to an authoritarian extent extending to a population control mechanism. This is a far more likely delivery mechanism for Rapid population reduction policies than any Vaccination regime, Famine equally, is a far more effective and efficient means of population reduction than certainly War or any other form of genocide, for the Authoritarian regime deploying it, it is also complete with a shield of plausible deniability.
Just my 10 cents per KW/h or my 100 euros/tonne of CO2
https://www.reuters.com/business/energy/europes-carbon-price-nears-100-euro-milestone-2022-02-04/
Just Saying.
DARK WINTER, CLADEX, EVENT201 #AADHAAR TO #IABATO YOU SAY #ARYANS I SAY #ARIANS
August 7, 2022 DARK WINTER, CLADEX, EVENT201 #AADHAAR TO #IABATO YOU SAY #ARYANS I SAY #ARIANS DARK WINTER, CLADEX, EVENT201 #AADHAAR EVENT 201 GIVEN ITS PROPER CONTEXT IS A MONETARY SYSTEM EVENT John at the Slog and I, had a long chat yesterday afternoon. My contention was that we had won this season’s league, we had yet to win the Cup and of course next …
Israel is getting ready to expand its borders. Covid 19 is a fraud, but it's served its purpose. We're distracted, in terror and not thinking. The "markers" in the virus have provided interesting data of transference mechanisms. Population movement is locked down - now for the real virus to wreak havoc? Or will it just blow over? Fabian Socialist style? We thought we were all gonna die! But they just wanted us in the right frame of mind for the Fed crypto app and a handout.
Expect a Fed crypto app - straight from The Fed to you.
Understand The Belt & Road and Israel's central role, and its move from a "protectorate" seeking protectors, to a regional power. That was what 911 was about. This is what COVID-19 is about.
This article lays it out for you: Bunting’s map and Israel on China’s new Silk Road - https://blogs.timesofisrael.com/buntings-map-and-israel-on-chinas-new-silk-road/
*An Economic Powerhouse and a Rising Hi-Tech Superpower – 25 Years of Diplomatic Relations Between China and Israel*
This January, Israel and China marked 25 years of diplomatic relations, a move that enabled cooperation in a variety of fields, peaking in recent years with joint activity in trade, tourism, healthcare, academia and technological R&D
https://blogs.timesofisrael.com/an-economic-powerhouse-and-a-rising-hi-tech-superpower-25-years-of-diplomatic-relations-between-china-and-israel/
https://altcensored.com/channel/UClD7vgcSgcrmqtkpHknp57Q
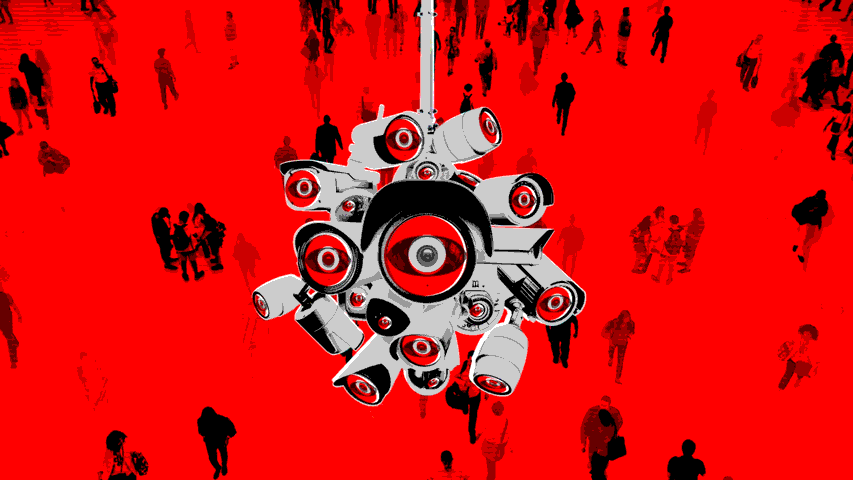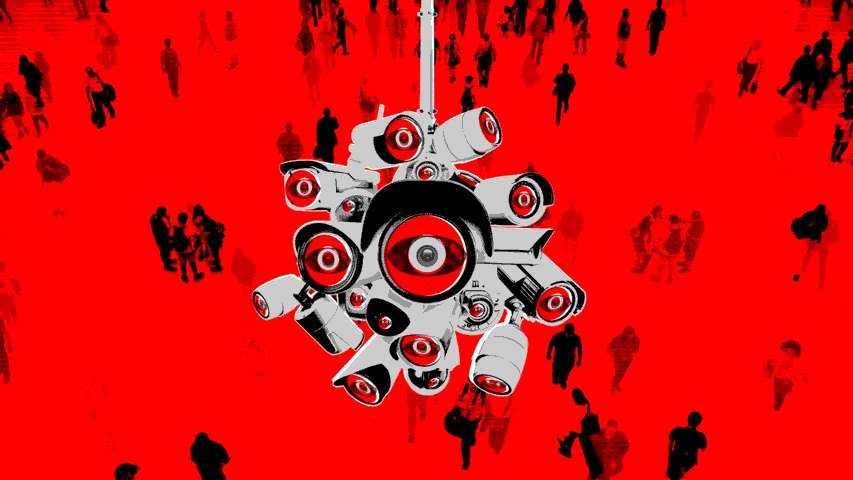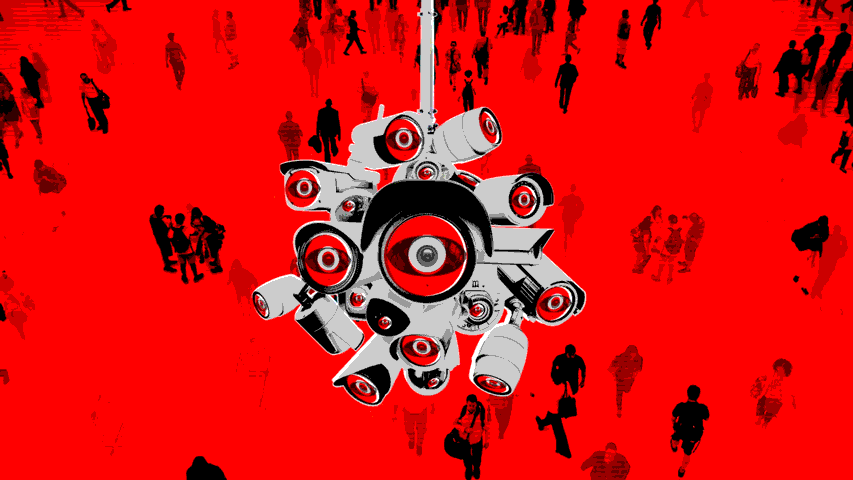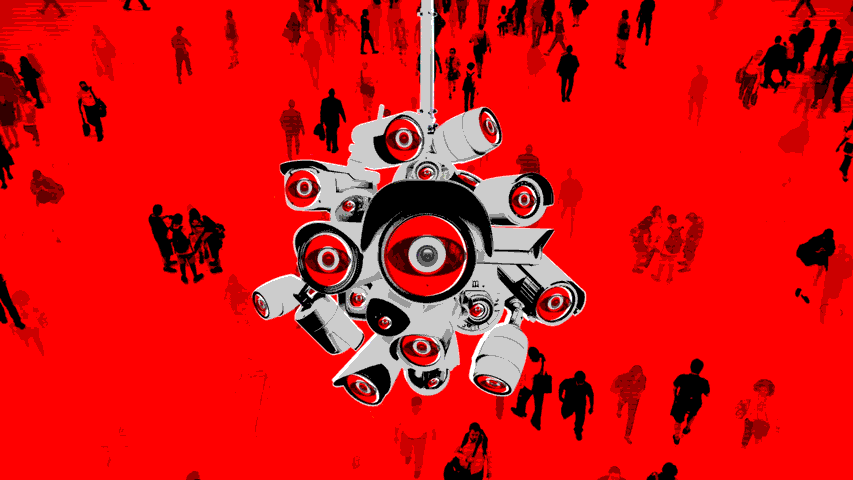
All Hail the Panopticon Jailer Bot. The Powers That Be, have a PJB
The enshittification of Linkedin. Enshittification is "...a seemingly inevitable consequence arising from the combination of the ease of changing how a platform allocates value, combined with the nature of a "two-sided market," where a platform sits between buyers and sellers, holds each hostage to the other, raking off an ever-larger share of the value t…